Most companies spend between 45%-55% of their IT budget on non-production activities like Training, Development & Testing and lose 20-40% of productivity across their software testing and software development lifecycle. This is because the art of “Test Environment Management” (or TEM) is still an area of significant confusion.
What is Test Environment Management? A Quick Definition
In the hope of educating and raising the bar on Test Environment Management, here’s a quick overview of “IT & Test Environment Best Practices” from Enov8.
Test Environment Management is the act of understanding your production environment and cross-life-cycle test environments. It includes establishing controls to ensure your teams use them effectively and rapidly, service, provision, and delete them on time.
Why Is the Test Environment Management Process Important?
In the ever-evolving IT/Software field, requirements continually change, creating a complex interplay between cost, quality, and time. While high-quality products can be achieved with adequate budget and time, projects often exceed these constraints, resulting in compromised product quality.
One reason for poor quality products is the inadequate prioritization and inefficient management of test environment management. Regulatory compliance, such as Sarbanes Oxley, underscores the importance of ensuring software and services comply with industry norms and business requirements.
Therefore, effective test environment management processes are crucial to delivering high-quality products within budget and time constraints.

Test Environment Hot Spots
Test environment hot spots are critical areas within a test environment that require special attention to ensure the smooth functioning of the environment. These hotspots can be any part of the environment that can potentially cause issues, such as configuration problems, resource allocation, or dependencies.
One of the most common hotspots is the hardware and infrastructure of the environment. It is crucial to ensure that the hardware is capable of handling the testing load and that it is adequately configured. For example, insufficient memory or storage can lead to performance issues, while inadequate network capacity can cause delays or interruptions in testing.
Another hotspot is the test data, which should be carefully managed to ensure it is accurate and relevant. Testing with incomplete or incorrect data can lead to false positives and false negatives, which can result in significant costs and delays.

Integration points with other systems, such as third-party applications, databases, and APIs, are also potential hotspots. It is essential to ensure that these integration points are thoroughly tested and validated, and that any changes to the system do not affect the functionality of the test environment.
Finally, the configuration and deployment of the application being tested are critical hotspots. Changes to the application code, software patches, and upgrades can impact the test environment and cause issues.
Therefore, it is necessary to have a reliable and repeatable deployment process, and to test the application thoroughly before deploying it to the environment.
To manage these hotspots effectively, it is essential to conduct regular assessments of the environment, identify potential issues, and implement best practices to address them.
This approach ensures that the test environment is reliable, effective, and supports the testing process as a whole.
The Enov8 Test Environment Use Case
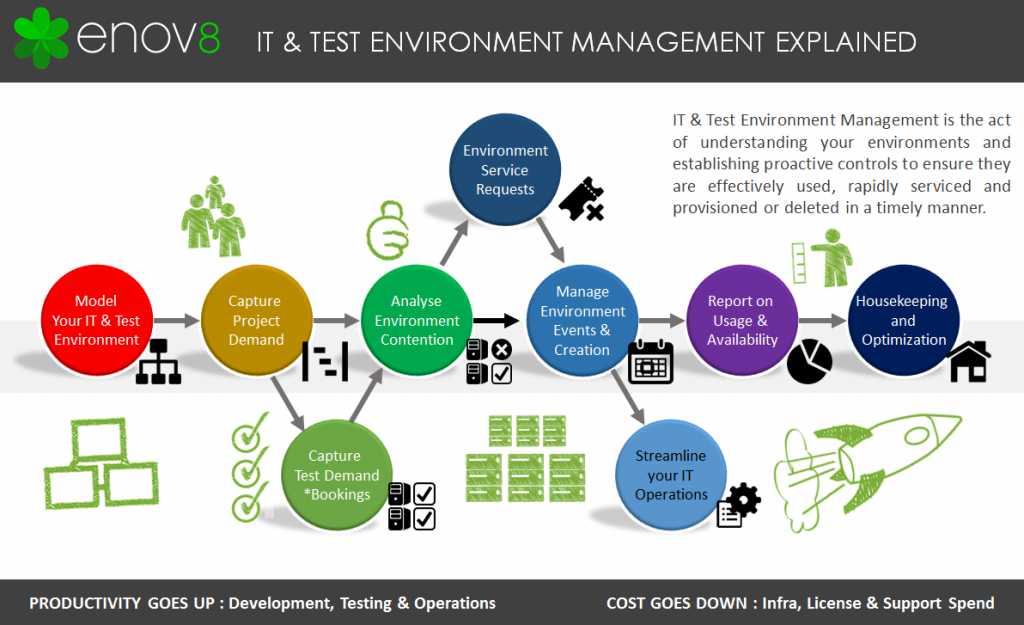
Key Test Environment Management Activities
Here is a list of the key TEM best practices you should consider implementing.
1. Knowledge Management / Modelling
Start with the process of modeling your Production Environment and Testing Environment. Including key configuration items like environment groups, systems, environment instances, components, microservices, relationships, and test data. It’s essential if we are to understand our platforms and end-to-end architecture truly.
Visualization and awareness contribute to better decision-making, servicing, and troubleshooting of our testing environment and help us better understand and support our production environment.
2. Demand Management
Development and software testing teams need access to specific test environments throughout the software development process. To avoid conflict and optimize the use of company resources, it is important to have a system in place that captures and manages demand for test environments.
This is where test environment booking management comes in.
Test environment booking management is a system that records the date, time, and duration of each team’s requested use of a test environment. You can use this information to schedule and allocate resources accordingly.
3. Streamline via Environment Automation
Invest in the orchestration (aka scripting) for key Test Environment tasks like Deployment Provisioning, Rollback, Decommissioning, and Test Bed Health checks.
Tip: If it takes more than an hour to prepare a test environment, there’s something wrong. Perhaps it is time to review your approach.

4. Testing Environments Planning & Coordination
The Test Environments Management process is responsible for managing and proactively scheduling test environment activities.
Use calendaring to coordinate operations across your test environments and ensure that you complete your testing environment preparation tasks in a timely and organized manner.
Tip: Attach the use of implementation plans (aka deployment plans) for more complex events. For example, create a ‘deployment implementation plan.’
5. Streamline via Standardised Operations
Use test environment run sheets and implementation plans to coordinate TEM operations and ensure test environment preparation tasks are completed in a timely and organized manner. Timely environments contribute to more software development and software testing time.
Tip: Employ this approach across all your Testing Environment tiers, i.e., Infrastructure, Applications, and Test Data. And across the lifecycle, i.e., the Software Development Environment, Test Environments like your Integration Testing Environment, Staging Environment, Performance Testing Environment, and of course, your Production Environments.
6. Optimize Through Insights
Drive continuous improvement through up-to-date insights on test environment behavior.
Use metrics, real-time data feeds, and dashboards to better understand your environment footprint, test environment usage, systems availability, and the various system teams’ service capability.
Watch Our TEM Video to Learn More
Conclusion
In conclusion, Test Environment Management (TEM) plays a crucial role in software development and testing. It is essential to manage and maintain the various testing environments to ensure the delivery of high-quality software. TEM enables effective collaboration between developers, testers, and other stakeholders and helps identify and mitigate potential risks early on in the development process.
By implementing a comprehensive TEM strategy, organizations can improve software quality, reduce downtime, and ultimately deliver better products to their customers.
With the growing complexity of software development and testing, TEM has become increasingly important, and it is essential for organizations to invest in effective TEM practices to stay ahead of the competition.

Author
Jane Temov is an IT Environments Evangelist at Enov8, specializing in IT and Test Environment Management, Test Data Management, Data Security, Disaster Recovery, Release Management, Service Resilience, Configuration Management, DevOps, and Infrastructure/Cloud Migration. Jane is passionate about helping organizations optimize their IT environments for maximum efficiency.
