Data Tokenization (for Data Security). What is it?
APR, 2023
by Andrew Walker.
Author Andrew Walker
Andrew Walker is a software architect with 10+ years of experience. Andrew is passionate about his craft, and he loves using his skills to design enterprise solutions for Enov8, in the areas of IT Environments, Release & Data Management.
In today’s digital age, data security and privacy are crucial concerns for individuals and organizations alike. With the ever-increasing amount of sensitive information being collected and stored, it’s more important than ever to protect this data from unauthorized access and breaches. One of the methods used to ensure data security is data tokenization.
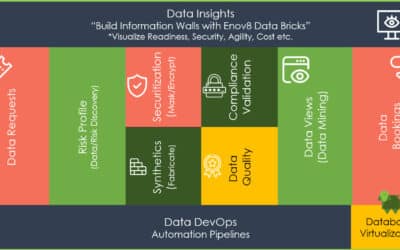
Enov8 Test Data Manager
*aka ‘Data Compliance Suite’
The Data Securitization and Test Data Management platform. DevSecOps your Test Data & Privacy Risks.
Data tokenization is a process that involves replacing sensitive data with a non-sensitive equivalent, known as a token. This token can be stored and processed without revealing the original data, making it a secure way to handle sensitive information. In this blog post, we’ll explore what data tokenization is, how it works, and its benefits. We’ll also take a look at how data tokenization is used in various industries and discuss some of the challenges and considerations involved in implementing it.
What is Data Tokenization?
Data tokenization is a technique used in data security to protect sensitive data by replacing it with a unique identifier or token. The token is then used in place of the original data in order to perform transactions or other operations, while the original data remains protected.
Tokenization is often used to protect credit card information, social security numbers, and other types of sensitive data. When a user enters sensitive information into a system, the system converts the data into a token and stores the token instead of the actual data. The token can then be used to process transactions, while the sensitive data remains secure.
One of the key benefits of tokenization is that it enables organizations to securely store and transmit sensitive data without exposing it to potential security breaches. In addition, because the token is not reversible, it is much more difficult for attackers to steal or use the original data.
Another benefit of tokenization is that it can help organizations comply with regulatory requirements, such as the Payment Card Industry Data Security Standard (PCI DSS), which requires that credit card data be protected.
Note: Although similiar Data masking & Tokenization are different. Data masking involves the substitution of sensitive data with fictitious data or scrambled values, which makes the original data non-reversible. On the other hand, tokenization replaces sensitive data with a unique identifier or token, while keeping the original data stored in a secure location, a vault, accessible only by authorized parties.
Data Tokenization Overview:
Benefits of Data Tokenization
Data tokenization offers several benefits over other data security methods. Here are some of the key advantages of using data tokenization:
- Increased security and privacy: Data tokenization is an effective way to protect sensitive information from unauthorized access and breaches. With data tokenization, the actual data is never stored, making it impossible for hackers to access the original information even if they gain access to the token.
- Flexibility and scalability: Data tokenization can be used with various types of sensitive information, including credit card numbers, social security numbers, and other personal identifying information. It can also be used with large datasets, making it a scalable solution for organizations of all sizes.
- Cost-effectiveness: Implementing data tokenization can be cost-effective, particularly when compared to other data security methods such as encryption. This is because data tokenization requires less processing power than encryption, resulting in lower costs for storage and processing.
- Compliance with regulations: Data tokenization can help organizations comply with various data security regulations, including HIPAA and PCI DSS. By using data tokenization, organizations can ensure that sensitive information is handled in a secure and compliant manner.
In summary, data tokenization offers several benefits, including increased security and privacy, flexibility and scalability, cost-effectiveness, and compliance with regulations.
How is Data Tokenization Used?
Data tokenization is used in various industries and applications, including:
- Finance: Data tokenization is used in the finance industry to protect sensitive financial information, such as credit card numbers and bank account details. By using data tokenization, financial institutions can ensure that sensitive information is protected from fraud and breaches.
- Healthcare: Data tokenization is used in the healthcare industry to protect patient data, such as medical records and personal identifying information. This helps healthcare organizations comply with HIPAA regulations and ensure that patient data is handled securely.
- E-commerce: Data tokenization is used in e-commerce applications to protect customer payment information, such as credit card details. By using data tokenization, e-commerce businesses can provide a secure and reliable payment experience for their customers.
- IoT devices: Data tokenization is used in IoT (Internet of Things) devices to protect sensitive data transmitted over the internet, such as device identification and user credentials. By using data tokenization, IoT device manufacturers can ensure that sensitive data is protected from unauthorized access.
Real-world use cases of data tokenization include:
- Google: Google uses data tokenization to protect user data in its cloud storage services. By using data tokenization, Google can ensure that user data is protected from unauthorized access.
- Target: Target uses data tokenization to protect customer payment information in its checkout system. This helps to prevent fraud and breaches, ensuring that customer data is handled securely.
In summary, data tokenization is used in various industries and applications, including finance, healthcare, e-commerce, and IoT devices. Real-world use cases of data tokenization include Google and Target.
Challenges, Considerations & Disadvantages
While data tokenization offers several benefits, there are also some challenges and considerations that organizations should be aware of when implementing this data security method. These include ensuring the security and integrity of the tokenization process, managing the lifecycle of tokens, choosing the right tokenization solution, complying with industry regulations, and the disadvantages of tokenization.
To ensure the security and integrity of the tokenization process, organizations must implement appropriate security measures, such as using strong encryption algorithms, restricting access to tokenized data, and regularly monitoring tokenization processes. Tokens have a finite lifespan, and organizations must manage their lifecycle to ensure proper deletion when no longer needed. Choosing the right tokenization solution depends on factors such as the level of security required, the type of sensitive data being tokenized, and the scalability of the solution. Organizations must also ensure that their tokenization processes comply with relevant regulations and standards.
The disadvantages of tokenization include the potential need for additional resources, such as processing power and storage, especially when tokenizing large data sets. Tokenization can increase complexity, making it more difficult to manage and maintain data, and may have legal implications in certain industries or applications. Additionally, the security of the token vault, which stores the mapping between the original data and the token, is critical to the security of the tokenized data. If the vault is compromised, hackers could potentially access the original data. Finally, tokenization is not foolproof and can still be susceptible to hacking attempts.
Conclusion
Data security and privacy are crucial concerns in today’s digital age. Data tokenization is one way to protect sensitive information from unauthorized access and breaches. Enov8 Test Data Manager offers a range of powerful methods, including data masking, data ciphering (reversible & non-reversible), and encryption methods, to help organizations implement robust data security measures. These methods can help organizations comply with industry regulations and ensure data security and privacy.
However, implementing data security measures can present some challenges, such as ensuring the security and integrity of the data security process, managing the lifecycle of data security measures, choosing the right data security solution, and complying with industry regulations. Organizations must carefully consider these factors when implementing data security measures and using tools like Enov8 Test Data Manager to protect sensitive information.
Other TDM Reading
Explore Test Data Management further:
Enov8 Blog: TDM Strategy Design Guide Best Practices
Enov8 Blog: Why TDM is so Important!
Enov8 Blog: What is Data Fabrication in TDM?
Relevant Articles
8 DevOps Anti-Patterns to Avoid
It’s the normal case with software buzzwords that people focus so much on what something is that they forget what it is not. DevOps is no exception. To truly embrace DevOps and cherish what it is, it’s important to comprehend what it isn’t. A plethora...
An Introduction to Application Rationalization
In today's fast-paced digital landscape, organizations often find themselves grappling with a sprawling array of applications. While these applications are crucial for various business operations, the lack of a structured approach to managing them can lead to...
What Makes a Great Test Data Management Tool
What Makes a Great Test Data Management Tool? In today's fast-paced IT landscape, having a robust Test Data Management (TDM) tool is crucial for ensuring quality, compliance, and efficiency in software development and testing. At Enov8, we pride ourselves on providing...
The Top Application Portfolio Management Tools
Managing an application portfolio is essential for organizations aiming to optimize their IT operations, reduce costs, and enhance overall efficiency. Application Portfolio Management (APM) tools are designed to help organizations achieve these goals by providing a...
What Is a Test Data Manager?
Testing is a critical aspect of software development, and it requires the use of appropriate test data to ensure that the software performs optimally. Test data management (TDM) is the process of creating, storing, and managing test data to ensure its quality,...
Sprint Scheduling: A Guide to Your Agile Calendar
Agile sprints can be a powerful, productive and collaborative event if managed properly. However, when neglected or set up incorrectly they risk becoming chaotic and inefficient. Crafting an effective schedule for your sprint is essential to ensure the success of your...