Implementing DevSecOps in your SDLC
MAY, 2023
by Andrew Walker.
Author Andrew Walker
Andrew Walker is a software architect with 10+ years of experience. Andrew is passionate about his craft, and he loves using his skills to design enterprise solutions for Enov8, in the areas of IT Environments, Release & Data Management.
In today’s rapidly evolving digital landscape, software development and security are more intertwined than ever before. Cybersecurity threats are becoming increasingly sophisticated, and traditional approaches to software development and security are no longer sufficient. To address this challenge, many organizations are turning to DevSecOps, a set of practices that integrate security into the software development lifecycle (SDLC). DevSecOps promotes collaboration and communication among all stakeholders, including developers, security professionals, and operations teams, to build secure software products. By implementing DevSecOps, organizations can improve the quality and security of their software products while reducing the risk of security breaches and vulnerabilities.
In this post, we will provide a comprehensive guide on how to implement DevSecOps in your SDLC, including the key principles and practices involved, steps to implement DevSecOps in your organization, best practices for successful implementation, and DevSecOps Anti-Patterns to avoid.
Overview of DevSecOps
DevSecOps is an approach to software development that integrates security into the entire SDLC. It emphasizes collaboration and communication among all stakeholders, including developers, security professionals, and operations teams, to build secure software products. DevSecOps seeks to shift security left in the SDLC, meaning that security is integrated into the process from the earliest stages of development, rather than being added as an afterthought. This approach promotes continuous security testing and analysis throughout the SDLC, including planning, coding, testing, deployment, and maintenance.
DevSecOps is based on several key principles and practices, including:
- Automation: Automated security tools and processes are used to identify and address vulnerabilities in real-time.
- Continuous integration and delivery: Security testing and analysis are integrated into the CI/CD pipeline to identify and address issues early in the SDLC.
- Collaboration and communication: All stakeholders work together to identify and address security risks and vulnerabilities.
- Risk management: Risks are identified and prioritized based on their potential impact, and security measures are implemented accordingly.
- Compliance: DevSecOps is aligned with regulatory and compliance requirements to ensure that software products meet the necessary standards.
By implementing DevSecOps, organizations can benefit from improved security posture, reduced risk of security breaches and vulnerabilities, increased efficiency and productivity, and improved customer satisfaction.
Steps to implement DevSecOps in your SDLC
- Identify your organization’s current SDLC and security processes: Before implementing DevSecOps, it’s essential to understand your organization’s current SDLC and security processes. This includes identifying the tools, technologies, and methodologies used in software development and security, as well as the roles and responsibilities of stakeholders involved in the process.
- Analyze your software development environment and identify potential security risks: The next step is to analyze your software development environment and identify potential security risks. This includes assessing your infrastructure, applications, and data for vulnerabilities, as well as understanding the threat landscape and potential attack vectors.
- Analyze your non-production/test data for risks: Non-production/test data can contain sensitive or personal data that should not be used in development or testing environments. Analyzing this data can help identify and secure sensitive data, reducing the risk of potential breaches or unauthorized access.
- Integrate security testing and analysis into each stage of the SDLC: Once potential security risks have been identified, it’s important to integrate security testing and analysis into each stage of the SDLC, from planning to deployment. This includes using automated security testing tools and processes to identify and address vulnerabilities in real-time.
- Implement automated security tools to identify and address vulnerabilities in real-time: Automated security tools and processes are critical to identifying and addressing vulnerabilities in real-time. These tools can include static analysis tools, dynamic analysis tools, and security scanning tools, among others.
- Establish clear roles and responsibilities for all stakeholders involved in the DevSecOps process: Clear roles and responsibilities for all stakeholders involved in the DevSecOps process are critical to its success. This includes establishing accountability for security issues, as well as providing training and education for all stakeholders involved.
- Provide continuous training and education for developers, security professionals, and operations teams: Continuous training and education for developers, security professionals, and operations teams are essential to maintaining the effectiveness of DevSecOps. This includes providing training on security best practices, emerging threats, and new technologies, among other topics.
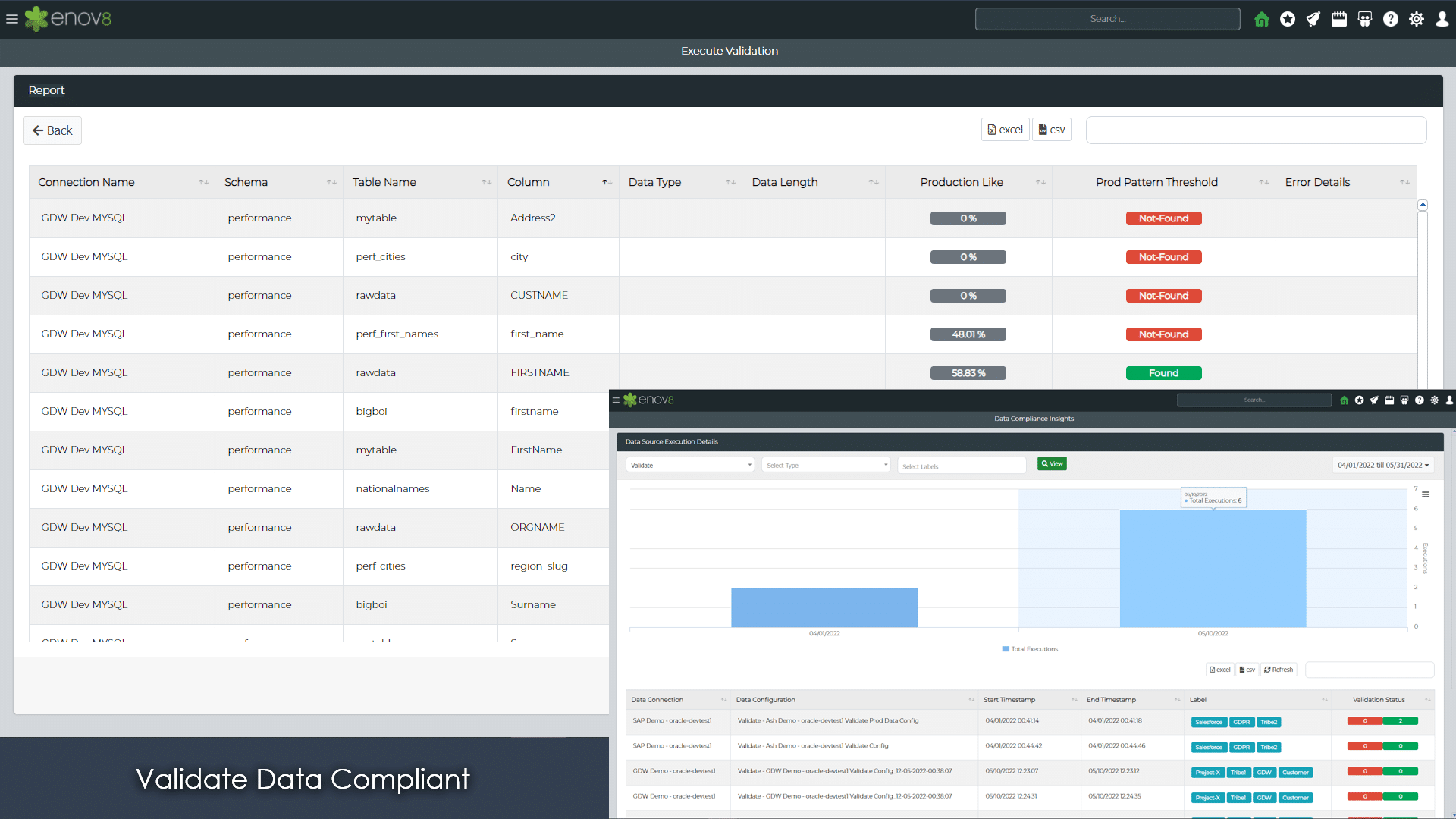
Enov8 TDM, Data Compliance Reports: Screenshot
Best practices for successful DevSecOps implementation
- Foster a culture of collaboration, communication, and shared responsibility: Collaboration, communication, and shared responsibility are essential to the success of DevSecOps. This includes promoting cross-functional teams, sharing knowledge and expertise, and encouraging open feedback and communication among stakeholders.
- Ensure executive buy-in and support for the DevSecOps initiative: Executive buy-in and support for the DevSecOps initiative are critical to its success. This includes aligning DevSecOps with the organization’s strategic goals, securing budget and resources, and promoting a culture of security.
- Encourage open feedback and continuous improvement: Continuous improvement is essential to the effectiveness of DevSecOps. This includes encouraging open feedback, conducting regular retrospectives and reviews, and addressing issues in a timely and effective manner.
- Regularly measure the effectiveness of the DevSecOps process and adjust as needed: Regularly measuring the effectiveness of the DevSecOps process is important to ensure that it is achieving its goals. This includes collecting and analyzing metrics, identifying areas for improvement, and adjusting the DevSecOps process as needed.
- Use security as code to automate security policy enforcement: Using security as code can help automate security policy enforcement, reducing the risk of human error and ensuring that security policies are consistently applied across the SDLC.
- Use infrastructure as code to automate environment provisioning and configuration: Infrastructure as code, through use of tools like Enov8’s Ansible Plugin, can help automate environment provisioning and configuration, reducing the risk of misconfiguration and ensuring that environments are consistent and secure.
By following these best practices, organizations can ensure the success of their DevSecOps implementation, improving the quality and security of their software products while reducing the risk of security breaches and vulnerabilities.
DevSecOps Anti-Patterns
- Lack of communication and collaboration among stakeholders: Lack of communication and collaboration among stakeholders can undermine the effectiveness of DevSecOps. This can lead to silos, misalignment of priorities, and a lack of shared responsibility for security.
- Overreliance on automated security tools without considering context and human oversight: Overreliance on automated security tools without considering context and human oversight can lead to false positives and false negatives, as well as missing important security issues.
- Failure to address security vulnerabilities early in the SDLC: Failure to address security vulnerabilities early in the SDLC can lead to increased costs and delays, as well as potential security breaches and vulnerabilities.
- Neglecting to perform regular security testing and analysis: Neglecting to perform regular security testing and analysis can lead to undiscovered vulnerabilities and risks, as well as security breaches and data loss.
- Lack of training and education for all stakeholders involved in DevSecOps: Lack of training and education for all stakeholders involved in DevSecOps can lead to a lack of awareness of security risks and best practices, as well as a lack of shared responsibility for security.
By being aware of these DevSecOps Anti-Patterns, organizations can take steps to avoid them and ensure the effectiveness of their DevSecOps implementation.
Conclusion
In today’s digital landscape, security is more important than ever, and traditional approaches to software development and security are no longer sufficient. DevSecOps provides a solution by integrating security into the SDLC, promoting collaboration and communication among all stakeholders, and emphasizing continuous security testing and analysis. By implementing DevSecOps, organizations can improve the quality and security of their software products while reducing the risk of security breaches and vulnerabilities.
To implement DevSecOps in your SDLC, it’s important to identify your organization’s current SDLC and security processes, analyze your software development environment for potential security risks, and integrate security testing and analysis into each stage of the SDLC. Additionally, following best practices such as fostering a culture of collaboration and communication, ensuring executive buy-in and support, encouraging continuous improvement, and regularly measuring effectiveness can help ensure the success of DevSecOps implementation.
It’s also important to be aware of DevSecOps Anti-Patterns, such as lack of communication and collaboration, overreliance on automated security tools, failure to address security vulnerabilities early in the SDLC, neglecting regular security testing and analysis, and lack of training and education for all stakeholders involved in DevSecOps.
By implementing DevSecOps and avoiding DevSecOps Anti-Patterns, organizations can benefit from improved security posture, reduced risk of security breaches and vulnerabilities, increased efficiency and productivity, and improved customer satisfaction.
Other TEM Reading
Enov8 Blog: What is Data Masking? And how do we do it?
Enov8 Blog: A DevOps Approach to Test Data Management
Enov8 Blog: Why TDM is so Important!
Relevant Articles
What is a Microservice Catalog? A Detailed Explanation
Microservices have revolutionized the way modern software systems are designed and developed. Breaking down complex applications into smaller, independently deployable services brings numerous benefits in terms of scalability, flexibility, and maintainability....
Delphix Alternatives: 7 to Consider in 2026
If you’re searching for delphix alternatives, you’re likely evaluating your test data management strategy. Delphix is widely recognized for data virtualization and masking, but it is not the only option available. As enterprise environments grow more complex and...
Enterprise Release Manager: A Guide to the Role
Do you want your company to scale efficiently? Look for an enterprise release manager (ERM). An ERM protects and manages the movements of releases in multiple environments. This includes build, test, and production environments. They ensure that there is a proper...
Data Governance Tools: 7 to Know in 2026
As data estates continue to grow in size and complexity, governance has shifted from a documentation problem to an execution problem. Data now spans cloud warehouses, operational systems, analytics platforms, streaming pipelines, and AI workflows, often owned by...
A Detailed Guide to Temenos Data Masking
Temenos powers core banking operations for financial institutions around the world. From customer onboarding and account management to payments and lending, it sits at the heart of highly regulated, data-intensive environments. That central role creates a challenge:...
Lower Environments: Understanding Their Role
Table of contentsWhat Is a Lower Environment?Types of Lower EnvironmentsWhy Lower Environments MatterClassical Architectural Assets for Lower EnvironmentsBenefits of Architectural Assets in Lower EnvironmentsUse Cases and ExamplesBest Practices for Implementing...