Unveiling the Power of Data Profiling
Aug, 2023
by Jane Temov.
Jane Temov is an IT Environments Evangelist at Enov8, specializing in IT and Test Environment Management, Test Data Management, Data Security, Disaster Recovery, Release Management, Service Resilience, Configuration Management, DevOps, and Infrastructure/Cloud Migration. Jane is passionate about helping organizations optimize their IT environments for maximum efficiency.
Introduction
In the ever-evolving landscape of software development and data management, ensuring the security of sensitive information has become paramount. Data breaches and privacy violations can result in not only financial losses but also irreparable damage to an organization’s reputation. This is where data profiling steps in as a powerful tool to identify potential security vulnerabilities and safeguard valuable data assets.
Enov8 Test Data Manager
*aka ‘Data Compliance Suite’
The Data Securitization and Test Data Management platform. DevSecOps your Test Data & Privacy Risks.
In this article, we’ll explore the significance of data profiling and delve into how Enov8’s automated data profiling capabilities play a vital role in bolstering data security.
The Significance of Data Profiling in Security
Data profiling is the process of analyzing and understanding the structure, content, and relationships within a dataset. This comprehensive analysis provides insights into the characteristics of the data, such as data types, patterns, distributions, and potential anomalies. While data profiling is often associated with data quality improvement, its significance in identifying security vulnerabilities cannot be overlooked.
Security vulnerabilities within datasets can range from inadvertently exposed Personally Identifiable Information (PII) to weak access controls that could potentially lead to unauthorized data access. Without a deep understanding of the data landscape, these vulnerabilities can remain hidden, posing a significant threat to an organization’s data security posture.
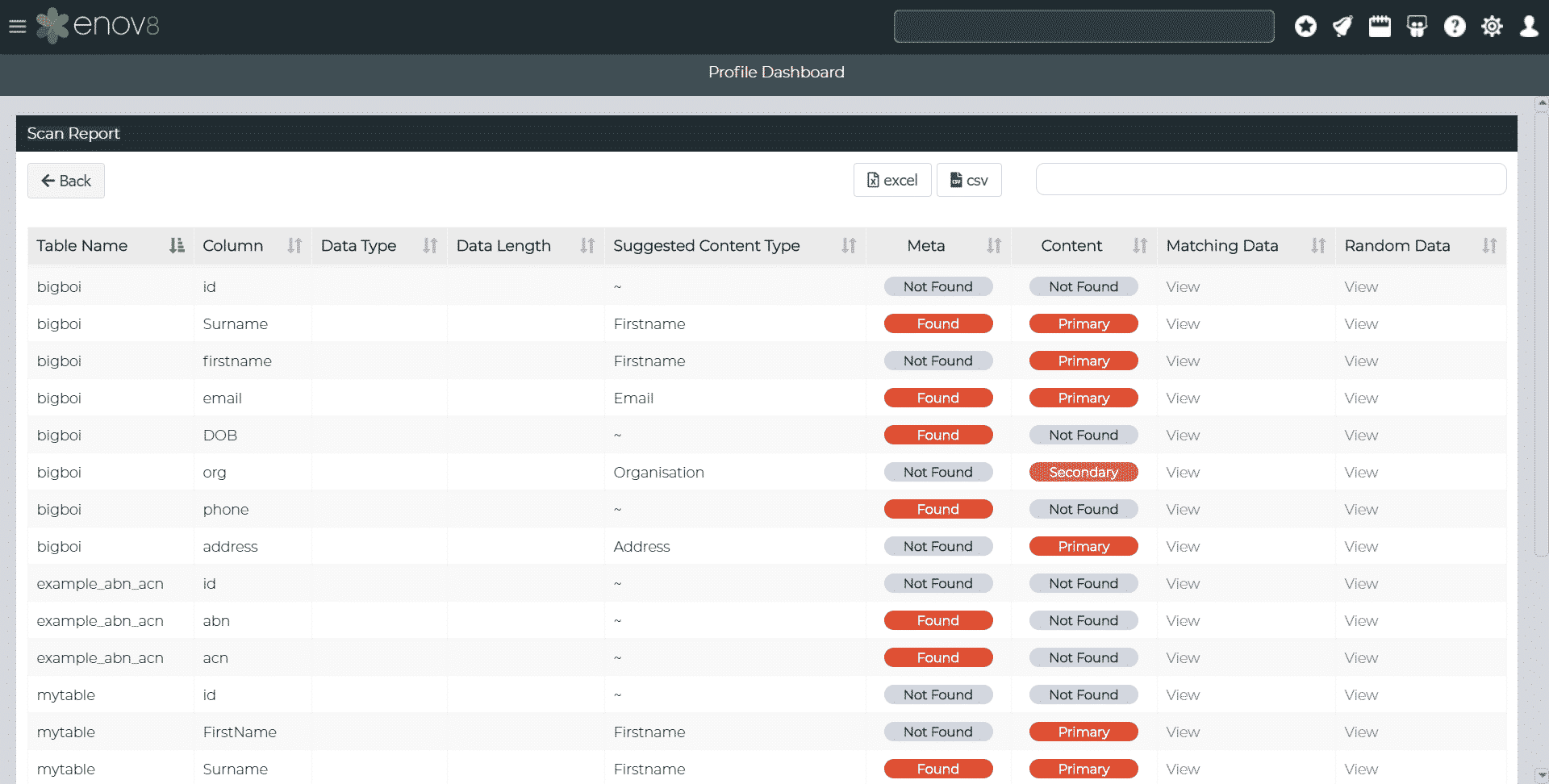
Automating Data Profiling with Enov8
Enter Enov8’s Test Data Manager and its advanced automated data profiling capabilities. With the power of Automation, Artificial Intelligence (AI), and Machine Learning (ML), Enov8’s Data Profiling module enables organizations to quickly understand their data and uncover risks that might lead to security exposures. Here’s how it works:
Rapid Understanding of Data
Manually analyzing vast datasets can be an overwhelming and time-consuming task. The automated data profiling feature of Enov8’s platform simplifies this process by rapidly analyzing the data, identifying PII and other sensitive data points.
Identifying Hidden Risks
The AI and ML algorithms employed by Enov8’s Data Profiling module allow it to pinpoint potential vulnerabilities that might be otherwise hidden within the data. This includes detecting PII and other sensitive customer data that needs special protection.
Real-time Insights
The insights provided by Enov8’s Data Profiling module act as a launchpad for enhancing data engineering practices. By offering real-time insights into the data landscape, organizations can proactively address security risks, leading to better data security practices.
Data Security and Compliance
With the increasing complexity of data security regulations like GDPR, HIPAA, and other privacy laws, having a tool that can efficiently identify and mitigate risks becomes critical. Enov8’s automated data profiling contributes to data compliance efforts by ensuring that sensitive data is identified and treated appropriately.
Strengthening Data Security with Enov8
The effectiveness of Enov8’s Data Profiling module extends beyond risk identification. It plays a crucial role in establishing a strong data security foundation. By automating the identification of vulnerabilities, organizations can take proactive measures, like Data Masking, to address them promptly. This not only reduces the likelihood of data breaches but also demonstrates a commitment to data protection and compliance.
Conclusion
In a world where data security breaches can have severe consequences, the power of data profiling cannot be underestimated. Enov8’s Test Data Manager, with its automated data profiling capabilities, plays a pivotal role in enhancing security by rapidly identifying potential risks within datasets. By harnessing the capabilities of Automation, AI, and ML, Enov8 empowers organizations to strengthen their data security posture, protect sensitive information, and maintain compliance with evolving regulations. As data security continues to be a top priority, leveraging tools like Enov8’s Data Profiling module becomes essential for ensuring a secure and resilient data environment.
Relevant Articles
Lower Environments: Understanding Their Role
Table of contentsWhat Is a Lower Environment?Types of Lower EnvironmentsWhy Lower Environments MatterClassical Architectural Assets for Lower EnvironmentsBenefits of Architectural Assets in Lower EnvironmentsUse Cases and ExamplesBest Practices for Implementing...
A Detailed Walkthrough of Oracle ERP Data Masking
Oracle ERP systems sit at the operational and financial core of large enterprises. They manage general ledger data, procurement and supplier records, payroll and HR information, and a wide range of transactional and reporting data that is both business-critical and...
Securing Microsoft Fabric Data for AI
Executive Summary Microsoft Fabric is rapidly becoming a core platform for enterprise analytics and AI. As organisations increasingly use Microsoft Fabric to support artificial intelligence and machine learning initiatives, the importance of protecting sensitive data,...
Dynamics 365 Data Masking: A Guide
Microsoft Dynamics 365 environments typically contain a mix of customer, financial, and operational data that is both business-critical and highly sensitive. While this data is essential for day-to-day operations, it also creates risk when copied into non-production...
Resilience Management: A Definition and Guide
Modern enterprises operate complex, interconnected systems where disruption is inevitable. Outages, failed releases, supplier issues, cyber incidents, and human error are no longer rare events but routine operational risks. In this environment, success is less about...
What is Release Management? An In-Depth Explanation
Do you want to ensure that your software releases meet the highest quality standards, while also satisfying security and compliance requirements? Release management is a crucial process that can help you achieve this goal. In today’s fast-paced business world, where...