How Enov8 Helps Financial Institutions Align with the EU’s Digital Operational Resilience Act

Executive Introduction
As of January 2025, the EU’s Digital Operational Resilience Act (DORA) has become legally binding for financial institutions operating across the European Economic Area. DORA represents a fundamental shift in how regulators view the resilience of financial services: not as an IT issue, but as a core business capability.
While the regulation spans five core pillars, the common thread across all of them is clear — data. The ability to identify, protect, and recover data across complex IT landscapes is now critical to achieving compliance. But DORA doesn’t just require protection; it demands operational proof — documented, testable resilience underpinned by strong governance.
This blog explores how Enov8’s platform addresses the often-overlooked data-related challenges of DORA, providing financial institutions with a clear path to compliance while supporting smarter, safer operations.
What is DORA?
The Digital Operational Resilience Act (DORA) is an EU regulation designed to ensure that financial institutions can maintain critical services during ICT disruptions, cyberattacks, or supplier outages. Unlike traditional data privacy laws (like GDPR), DORA focuses squarely on resilience: the capacity to prepare for, withstand, and recover from adverse digital events.
DORA applies to a wide range of regulated entities, including:
- Banks and investment firms
- Insurers and reinsurers
- Payment service providers
- Crypto-asset service providers
- ICT third-party service providers
The regulation breaks into five main pillars:
- ICT Risk Management – Proactive risk identification, classification, and mitigation
- ICT Incident Reporting – Timely reporting of major incidents to regulators
- Digital Operational Resilience Testing – Threat-led penetration testing and scenario simulations
- ICT Third-Party Risk – Governance over outsourcing and supply chain risk
- Information Sharing – Voluntary exchange of cyber threat intelligence
Data: The Cross-Cutting Concern
While each DORA pillar seems functionally distinct, data is the unifying asset underpinning compliance:
- Risk cannot be managed if you don’t understand your data exposure.
- Incidents can’t be reported without data lineage and traceability.
- Recovery is impossible without trusted, protected data copies.
- Third-party risk cannot be mitigated without controlling data flow and masking.
In other words: if you can’t govern your data, you can’t comply with DORA.
Common Gaps in Financial Institutions
Many financial institutions, especially those with legacy systems or complex delivery pipelines, face real challenges in aligning with DORA:
- Lack of Data Risk Profiling: Few firms can map where sensitive data exists across dev, test, and staging environments.
- Insecure Test Environments: Real production data is often copied into test systems without sufficient masking.
- Poor Visibility Across IT Landscape: Fragmented tools and spreadsheets fail to provide audit trails or real-time awareness.
- Manual Recovery & Reporting: Recovery plans often rely on out-of-date documentation or tribal knowledge.
- Third-Party Exposure: Vendors, system integrators, and testers often have excessive access to sensitive datasets.
These issues aren’t just operational inefficiencies — they’re regulatory liabilities under DORA.
The Role of Risk Profiling and Data Masking
Two core disciplines are essential to addressing DORA’s data-related expectations:
1. Risk Profiling
Financial institutions must identify and classify ICT assets based on their criticality and data sensitivity. This includes:
- Mapping data flows and ownership across environments
- Assessing the impact of data loss or corruption
- Classifying datasets by sensitivity (e.g., PII, payment, regulatory)
Without a clear understanding of where your risks are, resilience strategies will be misaligned and insufficient.
2. Data Masking
DORA mandates data minimization and protection-by-design, particularly when data is shared externally or used in testing.
Masking ensures:
- Real customer data is obfuscated in lower environments
- Exposure to external vendors is reduced
- Recovery exercises can be safely conducted with synthetic or protected data
Masking is not just a privacy control — it’s a resilience enabler. It reduces the blast radius of any breach and allows safe operational testing.
How Enov8 Helps
Enov8’s platform is uniquely positioned to support DORA compliance in the context of data governance, operational visibility, and environment control.
Here’s how Enov8 maps to DORA’s requirements:
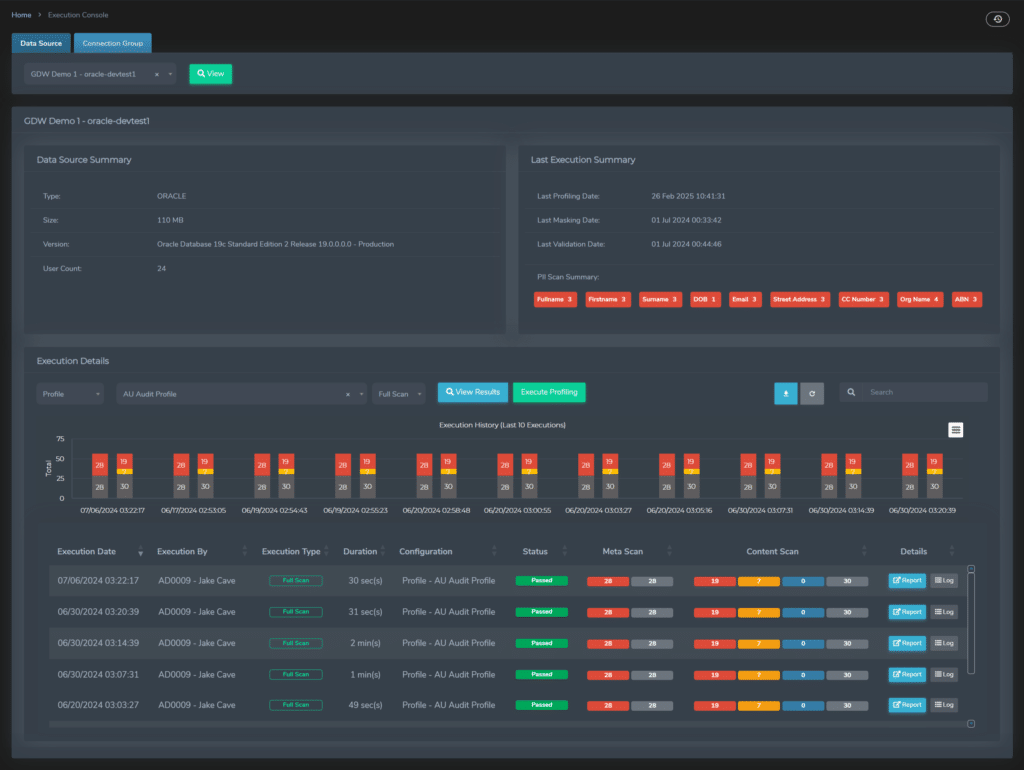
✅ Test Data Management (TDM)
- Automated data profiling and classification
- Integrated data masking and synthetic data generation
- Policy-driven access controls and audit trails
✅ Environment & Release Management
- Centralized visibility of all non-production environments
- Full environment booking, provisioning, and version tracking
- Integrated runbooks for planned and emergency recovery
✅ ICT Risk Governance
- Custom dashboards for risk status and mitigation tracking
- Evidence capture for resilience testing and compliance audits
- Real-time lineage of data flow, system dependencies, and access logs
✅ Third-Party Risk Mitigation
- Zoning of environments to enforce least-privilege access
- Secure data contracts for external testing and support teams
- Live monitoring of who accesses what, when, and where
By using Enov8, institutions can turn DORA compliance from a manual checkbox exercise into a live, automated governance layer.
The Strategic Value of Compliance
While DORA is mandatory, compliance can also unlock strategic value:
- Operational Efficiency: Streamlining environments, data provisioning, and testing reduces friction and cost.
- Improved Cyber Posture: Masked, segmented data reduces breach exposure.
- Faster Recovery: Defined runbooks and cloned environments improve MTTR (mean time to recovery).
- Regulator Trust: Demonstrating live dashboards and resilience scenarios builds regulator and board confidence.
Done well, DORA compliance becomes a competitive advantage, not a cost centre.
Conclusion: Data Resilience is the Battlefield
The digital battlefield has moved from networks to data. Regulators know that attackers exploit poor operational practices, and DORA is their response. It challenges financial institutions to rethink how they manage environments, safeguard data, and coordinate recovery.
At Enov8, we believe that resilience starts with visibility. If you can’t see it, you can’t govern it. And if you can’t govern it, you can’t comply.
Enov8 helps you take back control — of your data, your environments, and your operational risk.

Call to Action
Want to see how Enov8 helps you align with DORA?
Request a demo and explore:
- Automated data classification and masking workflows
- Environment insights and runbook automation
- Compliance dashboards tailored for DORA reporting
Visit www.enov8.com or contact us directly to start your DORA readiness journey.
