Ansible : How do I protect sensitive data with encrypted files
MAR, 2023
by Jane Temov.
Jane Temov is an IT Environments Evangelist at Enov8, specializing in IT and Test Environment Management, Test Data Management, Data Security, Disaster Recovery, Release Management, Service Resilience, Configuration Management, DevOps, and Infrastructure/Cloud Migration. Jane is passionate about helping organizations optimize their IT environments for maximum efficiency.
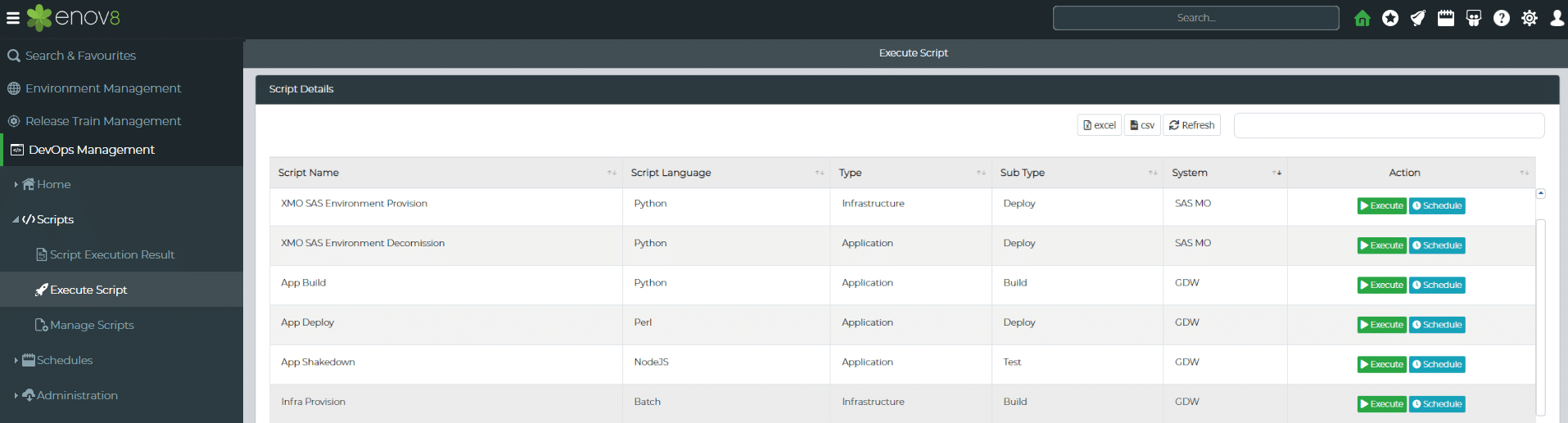
One of the great things about Enov8 Environment Manager is our DevOps Management area. An area that allows you to add your favourite automation independent of language. This includes the ability to “plug in” some very cool IT Automation tools like Ansible.
Enov8 IT & Test Environment Manager
*Innovate with Enov8
Streamlining delivery through effective transparency & control of your IT & Test Environments.
Ansible is an open-source automation tool used to manage and configure systems and applications. It uses a simple and powerful language to describe and automate IT workflows, making it easy to manage complex systems and processes with ease. Ansible is agentless, meaning it does not require any software or daemons to be installed on remote hosts, making it easy to deploy and use. With Ansible, IT teams can automate tasks such as configuration management, application deployment, and orchestration, allowing them to improve efficiency, reduce errors, and improve overall infrastructure reliability.
Protecting Sensitive Data with Encrypted Files
To protect sensitive data with encrypted files or elements in Ansible, you can use Ansible Vault. Ansible Vault is a feature in Ansible that allows you to encrypt sensitive data using a password, and then decrypt it when needed during playbook execution. Here are the steps to use Ansible Vault:
- Create a file that contains sensitive data, such as passwords, API keys, or private keys. For example, let’s say you have a file named
secrets.ymlthat contains the following:
username: myusername
password: mypassword
- Encrypt the file using the
ansible-vaultcommand:
ansible-vault encrypt secrets.yml
This will prompt you to enter a password that will be used to encrypt the file.
- Edit your playbook to include the encrypted file.
For example, let’s say your playbook includes the following task:
# yaml
– name: Configure the server
become: yesvars:
my_username: “{{ username }}”
my_password: “{{ password }}”template:
src: template.j2
dest: /etc/config.cfg
You can replace the username and password variables with the encrypted values by modifying the task as follows:
# yaml
– name: Configure the server
become: yes
vars_files:
– secrets.yml
vars:
my_username: “{{ username }}”
my_password: “{{ password }}”
template:
src: template.j2
dest: /etc/config.cfg
Note that we added the vars_files option to include the encrypted file.
- Run your playbook using the
ansible-playbookcommand and provide the password for the encrypted file:
python ansible-playbook playbook.yml –ask-vault-pass
This will prompt you to enter the password* you used to encrypt the file.
Once you enter the password, Ansible will decrypt the file and use the values in your playbook.
Tip: *Parameterising the Ansible Secret
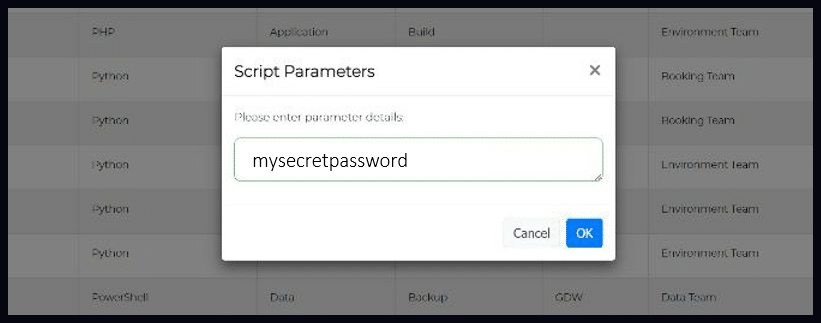
If you need to parameterise the secret then you can pass the password for the encrypted file as a parameter to the ansible-playbook command using the –vault-password-file option. For example, if your password is mysecretpassword, you can run the following command: ansible-playbook playbook.yml –vault-password-file=/path/to/password_file where /path/to/password_file is a file containing your password, such as: mysecretpassword. This can be particularly useful when you need to run the Enov8 environment automation on a schedule.
With these steps, you can protect sensitive data in your Ansible playbooks using Ansible Vault.
Enov8, DevOps Manager: Screenshot
Conclusion
In conclusion, Ansible Vault provides a powerful and flexible way to protect sensitive data in Ansible playbooks and configuration files. By encrypting sensitive data using strong encryption algorithms and protecting the decryption key with a password or key file, Ansible Vault helps ensure that critical data such as passwords, API keys, and other secrets are kept secure and confidential. Ansible Vault also integrates seamlessly with the rest of the Enov8 & Ansible automation framework, making it easy to incorporate secure credential management into your overall infrastructure management workflow. Overall, Ansible Vault is an essential tool for any organization that wants to ensure the security and integrity of its IT infrastructure and data.
Other TEM Reading
Interested in reading more about Test Environment Management. Why not start here:
Enov8 Blog: Your Essential Test Environment Management Checklist
Enov8 Blog: What makes a good Test Environment Manager
Enov8 Blog: Understanding the Types of Test Environments
Relevant Articles
A Data Loss Prevention Security Checklist for Enterprise
Companies today are collecting more data than ever and using analytics to influence everything from sales and marketing to research and development. In fact, data is now one of the most valuable assets that a company can own. Yet while data is more important...
Enterprise Architecture Principles: 13 for Resilience
Modern enterprises operate in environments defined by constant change. Cloud adoption, regulatory pressure, cybersecurity threats, distributed teams, and accelerating release cycles all increase the complexity of the IT landscape. In this environment, resilience is no...
Duck Creek Data Masking in Depth: A Guide
Insurance platforms are data-heavy by design. Customer identities, policy records, payment details, underwriting notes, claims histories. In a Duck Creek ecosystem, that data powers critical business processes across policy, billing, and claims. It also creates...
What is a Microservice Catalog? A Detailed Explanation
Microservices have revolutionized the way modern software systems are designed and developed. Breaking down complex applications into smaller, independently deployable services brings numerous benefits in terms of scalability, flexibility, and maintainability....
Delphix Alternatives: 7 to Consider in 2026
If you’re searching for delphix alternatives, you’re likely evaluating your test data management strategy. Delphix is widely recognized for data virtualization and masking, but it is not the only option available. As enterprise environments grow more complex and...
Enterprise Release Manager: A Guide to the Role
Do you want your company to scale efficiently? Look for an enterprise release manager (ERM). An ERM protects and manages the movements of releases in multiple environments. This includes build, test, and production environments. They ensure that there is a proper...